I have created a Site to Site VPN with a Fortigate to my virtual network in Azure.
Fortinet has supplied a guide how to do this. However, this guide is a little outdated, as the version of Fortigate is 5.2, an Azure is still in the classic Portal.
You can find the Guide here: Fortigate Manual Ipsec vpn to azure
This post, Uses the Azure ARM Portal and a Fortigate 30E with 5.4
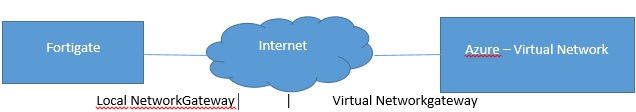
The design is as follows:
All magic happens in Azure in the Azure Menu:
The steps?
1. We have to create a Subnet in our virtual network.
2. Create A virtual networkgateway (thus a router in azure)
3. Create the local networkgateway (your local network/Fortigate)
3. Create a Virtual VPN connection between these 2 gateways
4. Create the IPSEC VPN tunnel in Fortigate
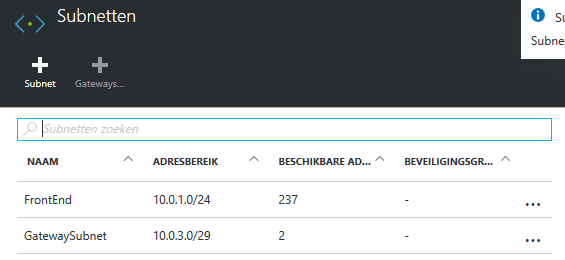
First things first, Create an additional VPN subnet in your network. The name has to be “GatewaySubnet” or your gateway will not be discovered by the virtual networkgateway.
The subnet is will be a /29, which will deliver 2 hosts.
After the subnet has been created you can go to Virtual Network Gateway.
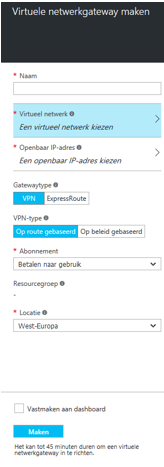
Select your Virtual network and a public IP. This Public IP has to be a static , and we’ll use this, later, to setup the vpn in the fortigate.
Next, create a local networkgateway, this will be the ‘fortinet’
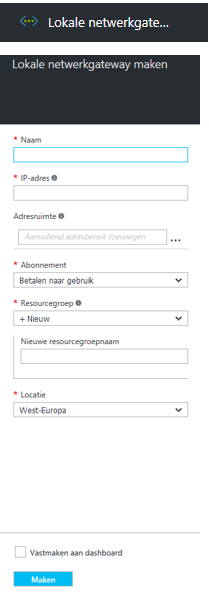
IP: IP location of your fortinet
PSK: the passphrase of your IPSEC vpn tunnel.
Next, will be to configure your fortigate.
I recommend, to create a site to site VPN, with the wizard.
Then you can change this to a custom tunnel.
According to the fortinet documententation:
NAT traversel: off
Dead peer connection: off
Key Lifetime Seconds Phase 1 : 56600
Diffe Hellman Group: 2
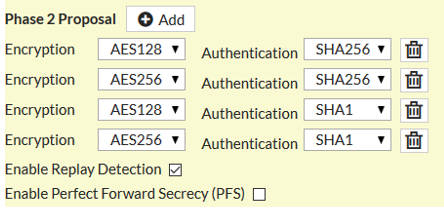
Phase 1 Proposal:
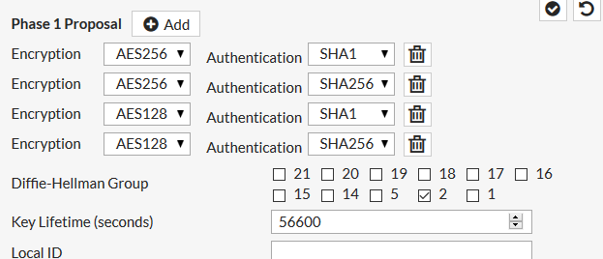
Auto-Negotiate: On
Autokey Keep Alive: On
Key Lifetime Seconds Phase 2: 7200
Thats it!